Shared Security Model in AWS explained | Cloud Computing
The AWS cloud security helps to protect confidentiality, integrity, and availability of data, systems & clients. Most companies trust Amazon Web Services because of their scalable and secure features and hence deploy their applications on it. Have you ever thought why companies need cybersecurity professionals or experts if they use AWS? Don`t you think Amazon should manage all this security?
This series of articles will help you to understand almost everything about the security of Amazon cloud computing services.
Amazon cloud services work on a shared security model. Shared security model, also known as AWS shared responsibility model.
Pre-requisite
Virtualization:
Virtualization deals with setting up a completely virtual environment to simulate hardware functionality. We create a virtual computer environment on the physical system by allocating the part of the physical resource components of that particular system. Virtualization takes place with the help of software like VMWare and Virtual Box.
The hardware components of server system get divided into multiple virtual components.
In this way, multiple operating systems, applications, networks can be deployed on a single system. As a whole, any virtual computer is called a virtual machine that behaves like a completely independent, isolated, and separate machine.
Why Virtualization?
The benefits of Virtualization in simple words are:-
- Cost-Effective: Virtualization lowers the cost of buying new hardware as multiple VMs can share a single server and its resources.
- Reduced Downtime: Since applications can use multiple VMs to the downtime also reduces.
- Hassle-free Management: As the complete machine can be managed via software only, Management becomes easy.
Also virtualization has laid the foundation for cloud computing.
Host Operating System:
The operating system on a physical computer or server enabling virtualization. The term host machine used for servers or physical machines.
Cloud computing
Before diving into cloud computing, you should know that communication traditionally uses a client-server model of communication. In this type of communication, one computer act as a server and another as a client. The user requests something like information or function and the server fulfills this request.
So what basically happens is that the information is stored in a physical server with hard disk storage in it. To access that information, requests have to be made from the client computer to the server computer every time. Also, it should be the responsibility of a user to not only configure client but server as well for all types of communication for a single application. For example for file sharing, web hosting, mail server setup, etc. Also, the cost of scaling up the resources increased because more physical components needed.
Now when we talk about cloud computing, the focus point changes. We instead of focusing on configuring services, we just focus on hosting the application as the cloud company takes the rest of responsibility.
Defining the cloud, we simply say that the cloud means the internet. And in cloud computing, we actually use a separate system for all types of transactions remotely.
Twist
In the case of traditional computing, the server means a physical computer and we knew both the endpoints (Sender & Receiver). But in the case of cloud computing, we only know our application and our system through which we access the other system remotely. The receiver end can be any physical server with a virtual machine with any configuration which can be scaled-up in clicks. We never know the exact endpoint of the receiver in cloud computing.
Concluding cloud computing, we define cloud as on-demand services from any shared infrastructure. The shared infrastructure is located somewhere on the internet. Now because we don’t have to worry about the location or handling, we find this service convenient & efficient as we only pay for what we use.
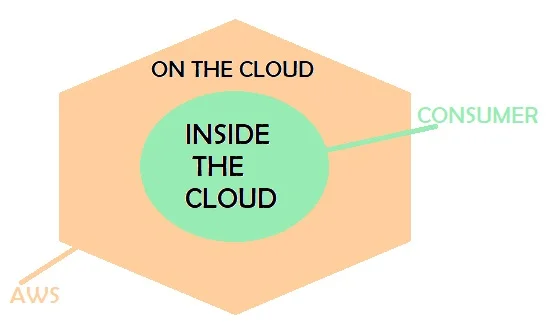
What is AWS Shared security model?
AWS shared security model ensures that both the parties i.e. Amazon and the consumer using their service must be equally responsible for securing the sensitive data of the consumer. In this model, Amazon takes responsibility to secure the cloud infrastructure and consumer takes the responsibility to secure deployed workload.

Role of AWS in securing the cloud in Shared Security Model
Primarily, AWS secures the global infrastructure of the cloud. This global infrastructure includes hardware & software, basically the physical level security. AWS manages the security of the availability zones and edge locations. Amazon also manages the services which provide the flexibility and scalability of cloud-based resources. Also, the protection during the calamity or natural disasters comes under the responsibility of AWS. All these responsibilities work primarily at the physical and infrastructure levels. Let us understand some of them:
- Hardware: Basically deals with Physical security controls and maintenance. Also includes the availability zones, edge location, and regions.
In AWS, the services get deployed regionally in geographical and self-contained areas that contain all physical resources required by any application. We call them regions. A region can be regarded as a cluster of data centres. A region may have isolated or multiple data centres. So we use the term Availability Zone as a logical data centre or group of data centres (Group treated as a single data centre)
Edge locations caches data and aim at reducing the distance from the customers i.e. the latency.
AWS maintain the data centres with facilities like cooling, power supply, etc.
- Software: The services related to network, compute storage and database. Few of these services including patch management and configuration management.
Remember Amazon provides tools and practices for security from the server-side. But consumers must implement them from the client-side.
Few of them are as follows:
- Network Security with the help of built-in firewalls, DDoS Mitigation, and TLS.
- Encryption features for adding an additional layer of security on databases & storage.
- Access management policies like multi-factor authentication, Identity access management, custom permissions.
- AWS also monitors logs and activities.
- AWS regularly performs audits compliant with various security guidelines and practices in accordance with different and multiple standards.
Role of the consumer in securing the cloud in Shared Security Model
Different consumers can have different responsibilities. Responsibilities depend on the type of service used including client-side implementation, management, and configurations.
As listen above, the consumers have to ensure the implementation of resources provided by Amazon including:
- Regularly updating the guest OS and the applications or software installed for major and minor updates and security patches.
- The physical configuration has already been done by Amazon. But the logical configuration of services needs to be done at the client-side.
- Setting up accounts with Strong credentials.
- Awareness and training of the employees using the cloud.
- System hardening of the instance which includes configuring the security groups.
- Setting up minimum required permissions for different users and IAM implementation.
- Defining rules for firewalls, VPNs & configuring the TLS.
I hope you got the idea of the concept of cloud computing and security of AWS.
Learn more about Technical SEO here
I will also soon be publishing it on GeeksforGeeks
48 thoughts on “Shared Security Model in AWS explained | Cloud Computing”
You must be logged in to post a comment.


1surrounded
1pockets
coursework support https://brainycoursework.com/
custom coursework writing service https://brainycoursework.com/
coursework help uk https://courseworkninja.com/
do my coursework online https://courseworkninja.com/
coursework planner https://writingacoursework.com/
coursework marking https://writingacoursework.com/
creative writing english coursework https://mycourseworkhelp.net/
do my coursework https://mycourseworkhelp.net/
coursework help https://courseworkdownloads.com/
coursework writing uk https://courseworkdownloads.com/
custom coursework writing https://courseworkinfotest.com/
data analysis coursework https://courseworkinfotest.com/
https://coursework-expert.com/
coursework plagiarism https://coursework-expert.com/
https://teachingcoursework.com/
coursework project https://teachingcoursework.com/
coursework writing service https://buycoursework.org/
coursework project https://buycoursework.org/
coursework psychology https://courseworkdomau.com/
coursework support https://courseworkdomau.com/
free online sex dating websites https://freewebdating.net/
dating personal https://freewebdating.net/
asians dating site https://jewish-dating-online.net/
cdff dating site login https://jewish-dating-online.net/
singles https://jewish-dating-online.net/
online dating sites https://free-dating-sites-free-personals.com/
adult singles dating site https://free-dating-sites-free-personals.com/
single ladies https://sexanddatingonline.com/
free dating apps https://sexanddatingonline.com/
online date https://onlinedatingsurvey.com/
free single dating online https://onlinedatingsurvey.com/
top date sites https://onlinedatingsuccessguide.com/
raluka https://onlinedatingsuccessguide.com/
japanese chubby https://onlinedatinghunks.com/
fdating https://onlinedatinghunks.com/
dating game https://datingwebsiteshopper.com/
top dateing sites https://datingwebsiteshopper.com/
dating sites in usa https://allaboutdatingsites.com/
free f https://allaboutdatingsites.com/
free dating net https://freedatinglive.com/
date sites free https://freedatinglive.com/
dating chat free https://freewebdating.net/
find single women https://freewebdating.net/
[…] is not available in shared environments prone to performance issues during traffic surges. Like AWS has elastic […]
[…] is not available in shared environments prone to performance issues during traffic surges. Like AWS has elastic […]
[…] is not available in shared environments prone to performance issues during traffic surges. Like AWS has elastic […]